Latest News
Realize up to a 406% ROI over on-premises and hosted solutions
Your server workloads are better together on Azure. Realize up to a ROI by up to 406% ROI over on-premises and hosted solutions @MicrosoftAzure for your Windows Server and SQL Server workloads. Subscribe now!
Commvault boosts capacity and performance with Windows Server and Azure
When you leverage Azure Hybrid Benefit while running Windows Server on @MicrosoftAzure, you can save on cost, free up capacity, and boost performance. Learn more with this short video about Microsoft customer #Commvault:
Modernize Endpoints A Zero Trust approach
Microsoft Zero Trust is a security model built on Microsoft intelligent security cloud and endpoint leadership. Remediation (with Microsoft Defender for Endpoint integration) and device configurations optimized for Zero Trust are all part of the journey. With the Zero Trust approach, you build a solid foundation with policy enforcement that has context about people and endpoints.
Review the infographic for a breakdown and get a link to sign up for an Endpoint Management workshop.
Just move it to the cloud
How you migrate your data to the cloud depends on many factors, but #Microsoft is here to help. Learn from this blog post about different methods of data migration and which one may be best for you.
A First Device Supported by Microsoft Endpoint Manager for Frontline Workers
Help is available to empower the frontline workforce with a seamless endpoint experience, tailored to the user consistently, on devices they need to get the job done. Travel restrictions accelerated the trend for hands-free remote expert guidance to frontline workers, and leaders witnessed the tremendous safety and productivity benefits of collaboration. With Microsoft Endpoint Manager, organizations can securely deploy RealWear devices to thousands more employees, using a modern Device Owner management model along with their smart phones and tablets.
Up-to-Date infographic
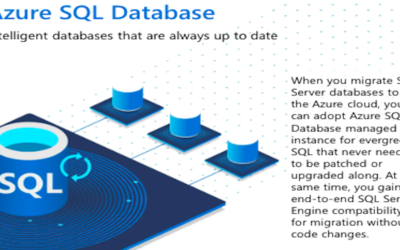
Spend less time on maintenance and more time on creation and innovation when you use #Microsoft #Azure SQL database. Its intelligent databases are always up to date with unique, built-in resource management and governance. Learn more with this infographic:
Reimagine your digital endpoint estate
Building resiliency for today’s new workplace means securing all devices—as well as enabling employee productivity and satisfaction.
Microsoft 365 enhances new business scenarios with products like Windows 365, Azure Virtual Desktop, Cloud Configuration, and Endpoint Manager. Did you know that Firmware security is built in on Microsoft Surface devices? Yes, that too. You can easily manage your resources while ensuring performance, productivity, and, most importantly, security.
Review the infographic and discover the key components that contribute to positive user experiences.
Reduce up to 80% in administration costs by offloading server/storage infrastructures
Offloading server/storage infrastructures to #Microsoft reduces up to 80% in administration costs. Subscribe now to learn how you can take advantage of these cost savings with #Azure.
Financial tech company gains SQL Server performance and scalability on Linux
As many startups grow, they encounter scaling challenges and latency. For dv01, a financial reporting and analytics company, Microsoft SQL Server provided the solution. Watch this video to learn how @MicrosoftAzure enabled faster response times and cut #dv01’s management time by 90%.
Deploy and protect endpoints for hybrid and frontline work
You can future-proof your organization and mitigate security risks with Microsoft 365. Products like Endpoint Manager, Azure Active Directory, and Microsoft Defender enable shared configured devices, streamlined deployments with zero-touch provisioning, secure, high-performance access, and much more. Review the infographic to learn about how hybrid and frontline workers can work more efficiently with a platform that is easy to manage, secure, and equipped with modern tools for a transformative business scenario.
Secure Infographic
Learn why companies choose #Azure for unmatched security, from @Microsoft’s 90+ compliance offerings to 3,500 dedicated security experts. Check out this infographic and contact Inspira Technology Group to learn more.
Unify management and security with Microsoft cloud, apps, and endpoints
Today’s workers require adaptability since they often use various devices to accomplish tasks. Microsoft cloud, apps, and endpoints combine services you may already be using, such as Microsoft Intune, which are part of the Microsoft 365 stack designed to help secure access, protect data, and respond and manage risk.
Use Endpoint Manager to deploy and configure apps to keep teams connected, apply Azure Virtual Desktop for fast, familiar access to internal resources, access Surface Hub to support a vast device ecosystem, and secure conditional access to mobile apps with Azure Active Directory.
Windows and SQL Server: The Best of Azure
Microsoft is the only cloud provider with end-to-end hybrid infrastructure. Check out this flyer to learn more about why Windows Server and SQL Server are best on #Azure, from one-stop support to unmatched security.
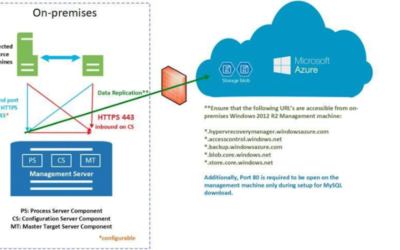
Security with Azure SQL Database in Azure Government
Microsoft commits to three main pillars in its advanced data security: data classification, vulnerability assessments, and threat detection. Learn more about Azure’s intelligent security capabilities with this episode from the Azure Government series.
REI embraces hybrid work with Microsoft Teams and Surface Hub
REI, the largest consumer cooperative in the United States, uses Microsoft Teams Connect capabilities to simplify how employees collaborate with people outside their organization. The company, for example, applies Microsoft Endpoint Manager and Intune in its strategy for protecting mobile devices. Moving to Microsoft 365 enabled employees more opportunities to use personal devices—and most importantly, to keep them secure. The freedom and flexibility of a hybrid or remote workforce with secure devices has also allowed the company to recruit and hire outside the Puget Sound area.
Cloud lessons learned: four companies that migrated their Windows Server and SQL Server workloads to Azure
Read the success stories of companies that increased workload performance and cut costs by moving their server workloads to @MicrosoftAzure. Learn how to find the migration path that’s best for your company with this eBook:
Carlsberg Group follows a recipe for success with Microsoft Azure, SAP, and a cloud-first strategy
Streamline your IT services with #Microsoft cloud migration. Discover how the #CarlsbergGroup successfully migrated to #Azure to get scalable, efficient, and secure IT for a digital solution to market. Watch this video to learn more.
Protect your endpoints with top EDR software
To function in a safer digital environment, companies must now consider endpoint detection and response software (EDR) enabled with AI and machine learning capabilities, as well as threat intelligence databases to minimize potential security breaches.
But most of the features that users expect, like device control, advanced threat targeting, and rollback, are either unavailable or come at extra cost. Microsoft Defender for Endpoints integrates into the source code of Windows, making it an obvious choice for its devices (also available for Mac and Linux).
The Total Economic Impact™ Of Microsoft Endpoint Manager
Microsoft Endpoint Manager is a solution that provides on-premises and cloud-based devices with tools (as well as the ability to co-manage with them) to provision, deploy, manage, and secure endpoints. It also enables insights into endpoint health and performance and remediates vulnerabilities in multiple areas—all while significantly reducing costs.
Microsoft Endpoint Manager gives organizations the enhanced control and monitoring to support employees with minimal impact on user experience while preventing data loss and applying Zero Trust best practices.
Subscribe to stay connected—we’ll help you ensure a more secure work environment throughout your organization.
Reduce Costs Infographic
Innovation has supplanted cost savings as the primary driver of cloud migration for many businesses. But moving to the cloud needs to make sense for your bottom line, too. Learn how #Microsoft #Azure offers unique cost savings with this infographic:
Deploy and protect endpoints for hybrid work environments
The workplace is evolving and requires an innovative approach for endpoint modernization. Microsoft is bridging employee experiences and security with modernized endpoints that enable organizations to adapt to today’s new world of work in a secure way across a range of key business scenarios.
Building security into apps and devices help reduce the threat of endpoint vulnerability for workers on the frontline, remote workers, in-office employees, and everything in between. Modernizing endpoints help advance to Zero Trust.
The new normal: Hybrid work means greater focus on endpoint security
Whether it’s a hybrid, remote, or in-office experience, endpoint vulnerabilities represent a real security risk. Companies must secure any potential access to their internal network from hacking and cyberattacks—which are more prevalent than ever.
How can organizations modernize to protect themselves against these threats?
Using Zero Trust within the context of Azure Active Directory as a foundation, anything connecting to your network must be validated before gaining access. And even when vetted, it will operate in a separate virtual machine to keep the rest of the network secure.
10 reasons to use Azure SQL in your next project
Are you and your team taking full advantage of Microsoft Azure SQL Server? Learn why this choice is the perfect one for your next project. Get an inside look at some of its unique new features from a member of the Azure SQL PM team: